BBCTF-2025
Sekure Notes (Web)
Challenge Description
Challenge: Sekure Notes
Category: Web
Author: vicevirus
URL: http://157.180.92.15:7999/
I don’t think you are able to get the flag. The captcha is too strong :(
Note: This challenge’s login is meant to be bruted. Check source code for which wordlist to use :)
Goals
- Bruteforce the admin password using the rockyou wordlist
- Bypass the CAPTCHA mechanism
- Exploit SSTI vulnerability to read the flag
Vulnerability Analysis
1. Hardcoded Admin Credentials
From the source code analysis, we can see the login function contains a hardcoded password check:
1 | def login(): |
The comment # rockyou indicates that the admin password is from the rockyou wordlist.
2. SSTI Vulnerability
There’s a Server-Side Template Injection vulnerability in the admin_notes() function:
1 | def admin_notes(): |
The vulnerability exists because:
- User input is directly passed to
render_template_string() - The
|safefilter is used, which tells Jinja2 not to escape the content - This allows arbitrary template injection
3. Weak CAPTCHA Implementation
The CAPTCHA can be bypassed using OCR since it generates simple alphanumeric text without complex distortions.
Solution
Step 1: Download and Analyze Source Code
- First, download the source code provided by the challenge
- Analyze the code to identify vulnerabilities and attack vectors
Step 2: Brute Force Attack with CAPTCHA Bypass
Since we need to bypass the CAPTCHA that appears on each login attempt, I discovered that the CAPTCHA in this challenge generates simple alphanumeric text that can be solved using OCR (Optical Character Recognition).
Attack Script:
1 | import requests |
How the Script Works:
CAPTCHA Solving (
solve_captchafunction):- Downloads the CAPTCHA image from the server
- Preprocesses the image (grayscale + binarization) for better OCR accuracy
- Uses Tesseract OCR to extract the 5-character alphanumeric text
- The CAPTCHA uses simple text generation, making it vulnerable to OCR
Login Brute Force (
attempt_loginfunction):- For each password from rockyou.txt, solves the CAPTCHA using OCR
- Submits login form with username=admin, password, and OCR-solved CAPTCHA
- Checks for successful login by detecting
/admin/notesin response URL
SSTI Exploitation (
exploit_sstifunction):- Once authenticated, exploits the template injection vulnerability
- Executes system commands to search for and read the flag
Step 3: Running the Attack
- Run the script against the target:
http://157.180.92.15:7999/ - The script will bruteforce passwords and find: peaches
- After successful login, it automatically exploits SSTI to get the flag
Step 4: Manual SSTI Exploitation (Alternative)
If you prefer manual exploitation after getting the credentials:
- Login with
admin:peaches - Navigate to the admin notes page
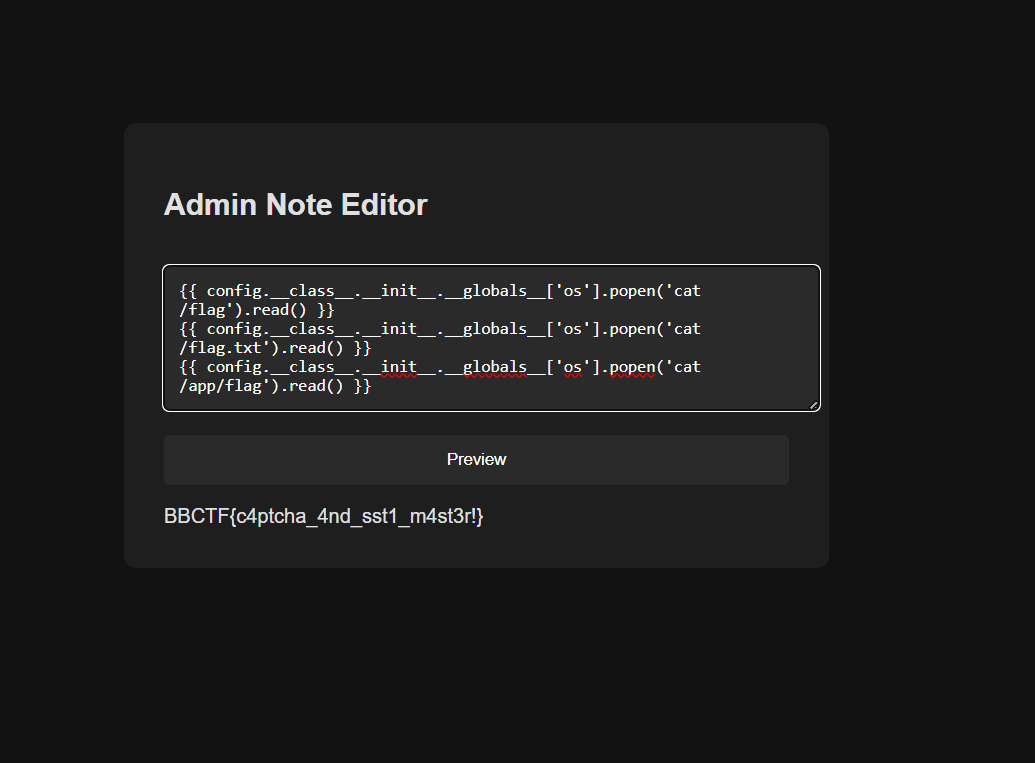
- Use one of these SSTI payloads to read the flag:
Payload:
1 | {{ config.__class__.__init__.__globals__['os'].popen('cat /flag.txt').read() }} |
Key Takeaways
- Weak CAPTCHA Implementation: The challenge demonstrates how simple text-based CAPTCHAs can be easily bypassed with OCR
- Source Code Analysis: Always check for hints in source code comments (like the
# rockyoucomment) - SSTI via |safe Filter: The
|safefilter in Jinja2 disables escaping, making template injection possible - Defense: Use proper input validation, complex CAPTCHAs, and avoid
|safefilter with user input
Final Result
Flag: BBCTF{c4ptcha_4nd_sst1_m4st3r!}
- Title: BBCTF-2025
- Author: Lee Wei Xuan
- Created at : 2025-05-12 03:03:43
- Updated at : 2025-11-26 03:14:08
- Link: https://weixuan0110.github.io/2025/05/12/BBCTF-2025/
- License: This work is licensed under CC BY-NC-SA 4.0.