Technical Analysis of Android Malware - Banking Trojan
Introduction
During a routine security intelligence exchange with my senior Ann from CyberX, I received a suspicious Android application package (APK) for analysis. The sample, disguised as a legitimate banking application (maybank2u.apk), demonstrated significant malicious capabilities warranting a comprehensive technical investigation.
Malware Investigation Report: Android Banking Trojan
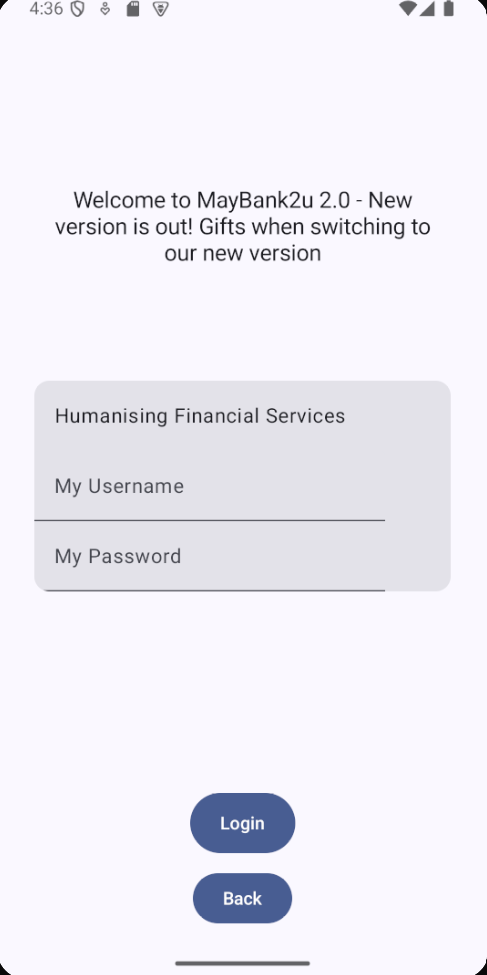
First Page
Stay at this page after login with anything
Executive Summary
This technical analysis documents a sophisticated Android banking trojan (maybank2u.apk) designed to intercept and exfiltrate sensitive information from compromised devices. The malware demonstrates advanced capabilities including:
- SMS Interception: Captures one-time passwords (OTPs) and authentication codes
- Data Exfiltration: Transmits stolen data to command and control (C2) infrastructure
- Persistence Mechanisms: Implements auto-start on boot and foreground services to maintain presence
- Anti-Analysis Techniques: Uses multi-layer obfuscation to evade detection
| Risk Assessment | Details |
|---|---|
| Severity Level | 🔴 CRITICAL |
| Impact Vector | Financial fraud, account takeover, data theft |
| Targeting | Banking applications, financial services users |
| Distribution | Phishing, fake app stores, smishing campaigns |
Technical Analysis
1. Malware Identification
| Attribute | Details |
|---|---|
| Package Name | maybank2u |
| Targeted Data | SMS messages, Android ID, device information |
| C2 Server | https://weedoom.net/multipush (HTTPS POST) |
| Obfuscation | Layered (Base64 + custom encoding via b() function) |
2. Key Malicious Components
The malware architecture consists of four primary components working in concert:
2.1 MainActivity
- Primary entry point disguised as a legitimate banking application
- Initializes malicious services upon launch
- Requests critical permissions for malicious functionality
2.2 SMS Interceptor (RE Class)
- Implements
BroadcastReceiverfor SMS interception - Extracts message metadata including:
- Sender phone number
- Message body content (targeting OTPs)
- Precise timestamp
- Implements offline persistence via
SharedPreferencesstorage
2.3 Data Exfiltration Module (C0044Fe Class)
- Handles communication with command and control server
- Implements custom obfuscation algorithms
- Manages authentication and device identification
2.4 Persistence Mechanism (SE Service)
- Runs as a foreground service with system notification
- Ensures continuous operation after device reboot
- Implements resilience against battery optimization
3. Data Exfiltration Workflow
The malware implements a sophisticated data exfiltration pipeline:
- Collection: Intercepts SMS messages via the
REbroadcast receiver - Processing: Extracts and parses message content, sender, and timestamp
- Obfuscation: Applies custom encoding algorithm (
b()function) to evade detection - Transmission: Sends data to C2 server via HTTPS POST requests
HTTP Request Details
Endpoint: https://weedoom.net/multipush
Headers:
1 | Content-Type: application/json |
Payload Structure:
1 | { |
4. Indicators of Compromise (IOCs)
The following artifacts can be used to identify infections and for threat hunting:
| Type | Value | Description |
|---|---|---|
| C2 Domain | weedoom.net | Primary exfiltration server |
| URLs | https://weedoom.net/multipush | SMS data exfiltration endpoint |
https://weedoom.net/minit | Initialization endpoint | |
| Key Strings | aHR0cHM6Ly93ZWVkb29tLm5ldA== | Base64-encoded C2 domain |
| Permissions | RECEIVE_SMS, READ_SMS, INTERNET | Critical permissions for functionality |
| Package | m.m.ml | Malware package identifier |
5. Attack Chain Visualization
The following diagram illustrates the complete attack flow from initial infection to data exfiltration:
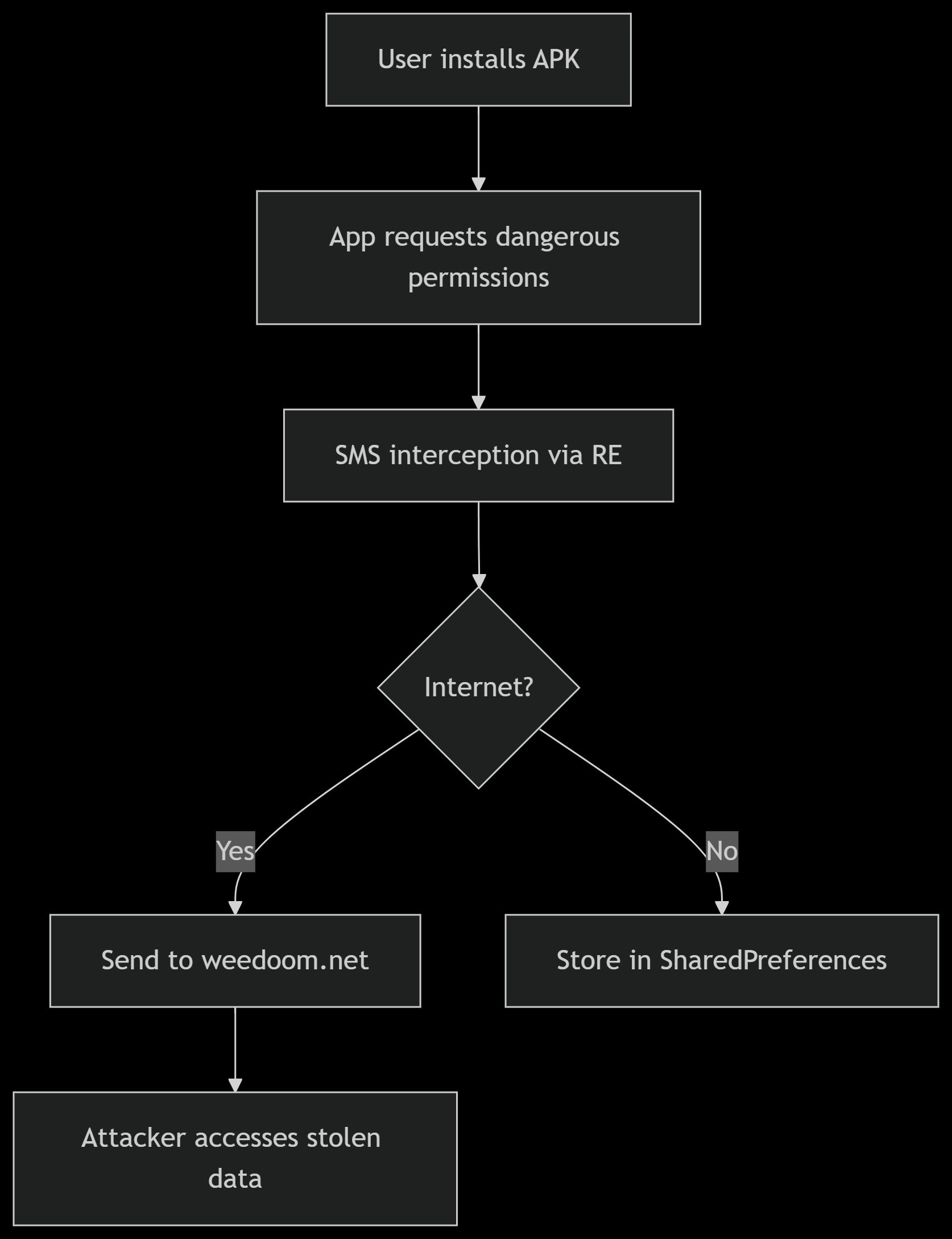
6. Technical Assessment
This malware represents a sophisticated banking trojan with significant capability to compromise financial transactions:
- Primary Objective: Intercept authentication messages (OTPs, 2FA codes)
- Infrastructure: Well-established command and control server (
weedoom.net) - Persistence: Multiple mechanisms to ensure continued operation
- Evasion: Multi-layered obfuscation techniques to avoid detection
6.1. Required Android Permissions
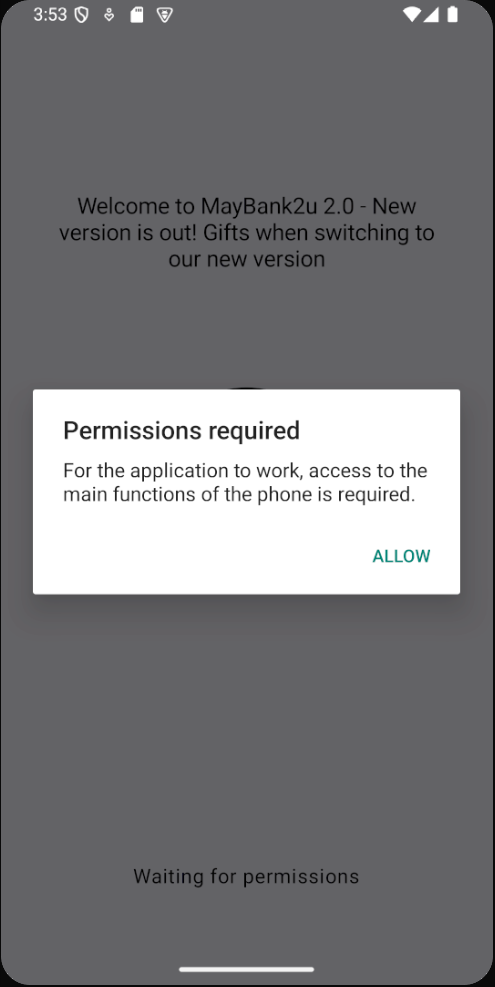
The malware requires critical permissions that enable its core functionality:
| Permission | Purpose |
|---|---|
RECEIVE_SMS | Interception of incoming SMS messages |
READ_SMS | Access to message content and metadata |
INTERNET | Exfiltration of stolen data |
RECEIVE_BOOT_COMPLETED | Persistence after device restart |
FOREGROUND_SERVICE | Maintain background operation |
 | |
 |
6.2. Core Exfiltration Logic
The primary exfiltration mechanism (C0044Fe.d()) implements sophisticated data transmission:
Key Implementation Steps in d(JSONObject jSONObject, boolean z)
A. Command & Control URL Preparation
1 | // Decode the obfuscated C2 domain |
The malware leverages two distinct C2 endpoints:
/multipush: Primary data exfiltration endpoint/minit: Initial communication/configuration endpoint
B. HTTP Request Configuration
1 | // Initialize HTTP request object |
The malware implements standard web communication:
- Method: POST
- Content-Type: application/json
C. Authentication Header Implementation
1 | // Decode authentication token from Base64 |
D. Device Identification Mechanism
1 | // Retrieve unique Android device identifier |
6.3. SMS Interception Implementation
A. Permission Validation and Broadcast Monitoring
1 | // Verify required permissions and validate broadcast intent |
The malware implements multiple validation checks:
- Permission Check: Verifies both
RECEIVE_SMSandREAD_SMSpermissions - Intent Filtering: Only processes
android.provider.Telephony.SMS_RECEIVEDbroadcasts
B. Message Extraction Mechanism
1 | // Extract all SMS messages from the broadcast intent |
C. Data Obfuscation Implementation
1 | // Apply obfuscation to timestamp |
The malware uses a proprietary obfuscation function (b()) to protect exfiltrated data from network inspection and detection systems.
6.4. Data Storage & Exfiltration Mechanisms
A. Offline Data Storage Implementation
1 | // Initialize SharedPreferences for persistent storage |
The malware implements resilient offline storage using Android’s SharedPreferences API:
- Storage Key:
"data" - Storage Mode: Private (mode
0) - Data Format: JSON objects in a
HashSet
JSON Storage Structure:
1 | { |
B. Online Exfiltration Implementation
1 | // Check for network connectivity |
The malware prioritizes immediate exfiltration when online, sending data with:
- Authentication: Obfuscated
"Beta"token - Device Identification: Obfuscated Android ID
- Transport: HTTPS POST to
weedoom.net/multipush
C. Network Connectivity Verification
1 | // Get system connectivity service |
The malware implements comprehensive network validation by checking multiple transport types:
- WiFi:
NetworkCapabilities.TRANSPORT_WIFI(1) - Cellular:
NetworkCapabilities.TRANSPORT_CELLULAR(0) - VPN:
NetworkCapabilities.TRANSPORT_VPN(3)
7. Core Functionality Summary
| Component | Implementation | Purpose |
|---|---|---|
| Permission Validation | AbstractC0737lq.s(context, "android.permission.RECEIVE_SMS") == 0 | Verify required system access |
| SMS Data Extraction | Telephony.Sms.Intents.getMessagesFromIntent(intent) | Capture incoming message content |
| Data Obfuscation | C0044Fe.b(str) | Encrypt/encode sensitive data |
| Offline Storage | sharedPreferences.edit().putStringSet("data", hashSet2).apply() | Cache data when network unavailable |
| Network Exfiltration | new C0044Fe(context, 1).d(new JSONObject(...), false) | Transmit data to command & control server |
8. Conclusion & Recommendations
This analysis confirms the presence of a sophisticated banking trojan targeting financial applications. The malware demonstrates advanced capabilities for SMS interception and data exfiltration with resilient operation even in adverse network conditions.
Security Recommendations:
Immediate Response:
- Factory reset affected devices
- Change passwords for all financial accounts
- Enable additional security measures for banking applications
Detection & Prevention:
- Monitor network traffic for connections to
weedoom.net - Implement SMS filtering/monitoring for sensitive accounts
- Deploy mobile threat defense solutions in corporate environments
- Monitor network traffic for connections to
User Education:
- Install applications only from official app stores
- Verify app permissions before installation
- Enable Google Play Protect on Android devices
9. Additional Technical Appendix
Technical Appendix: Decompiled Code Analysis
This document provides a detailed technical analysis of the decompiled code components from the malicious Android banking trojan (maybank2u.apk). The analysis reveals sophisticated mechanisms for SMS interception, data obfuscation, and C2 communication.
1. Main Entry Point (MainActivity.java)
The MainActivity class serves as the primary entry point for the malware, implementing several key initialization routines:
1 | package m.m.ml; |
Key Observations:
- Deceptive Permission Request: The malware presents a localized dialog to trick users into granting sensitive permissions, adapting to the device’s language settings
- Multi-language Support: Implements Russian and English localization to target a wider audience
- Persistence Mechanism: Starts a background service (
MgRKn55kcebb482e4b514772964e31012d0b1157.class) for continuous operation - Runtime Permissions: Uses modern Android permission request mechanisms to access sensitive data
2. SMS Interception Component (RE.java)
The RE class extends BroadcastReceiver to implement the core SMS interception functionality:
1 | public final class RE extends BroadcastReceiver { |
Key Observations:
- Event Targeting: The malware specifically targets
"android.provider.Telephony.SMS_RECEIVED"broadcasts - Comprehensive Data Collection: Extracts timestamp, sender, and full message content from each SMS
- Resilient Operation: Implements offline storage when network connectivity is unavailable
- Smart Exfiltration: Attempts to send previously stored data when connectivity is restored
3. Data Exfiltration Engine (C0044Fe.java)
The C0044Fe class implements sophisticated data obfuscation and exfiltration capabilities:
1 | public final class C0044Fe implements InterfaceC0004Ae { |
Key Observations:
- Multi-layer Obfuscation: Implements Base64 encoding followed by a custom character substitution cipher
- Embedded C2: Contains hardcoded Base64-encoded C2 domain (
aHR0cHM6Ly93ZWVkb29tLm5ldA===https://weedoom.net) - Dual Endpoint Strategy: Uses different endpoints for data exfiltration (
/multipush) and initialization (/minit) - Device Fingerprinting: Transmits unique Android device identifier with each request
- Silent Failure: Implements empty exception handler to prevent error notifications
4. Obfuscation Analysis
The malware employs a sophisticated custom character substitution cipher in the b() method:
1 | public static String b(String str) { |
Key Observations:
- Multi-alphabet Support: The cipher handles Latin, Cyrillic, and numeric characters differently
- Character Set Segregation: Different transformation algorithms for lowercase, uppercase, and digit characters
- Modular Arithmetic: Uses modulo operations to ensure character transformations remain within valid ranges
- Preservation of Special Characters: Non-alphanumeric characters remain unchanged
5. Network Transport Implementation
The malware implements sophisticated network connectivity detection to ensure reliable data exfiltration:
1 | // Get system connectivity service |
Key Observations:
- Comprehensive Connectivity Check: Tests multiple network transport types (WiFi, Cellular, VPN)
- Modern API Usage: Uses
NetworkCapabilitiesrather than deprecated connectivity methods - Transport Type Constants: References transport types by numeric constants:
- WiFi:
NetworkCapabilities.TRANSPORT_WIFI(1) - Cellular:
NetworkCapabilities.TRANSPORT_CELLULAR(0) - VPN:
NetworkCapabilities.TRANSPORT_VPN(3)
- WiFi:
6. Data Storage Schema
The malware implements resilient offline storage using Android’s SharedPreferences:
1 | // Initialize SharedPreferences for persistent storage |
Key Observations:
- Database Name: Uses generic name
"db"to avoid detection - Storage Mode: Uses private mode (0) to prevent access by other applications
- Data Structure: Stores JSON strings in a
HashSetunder key"data" - Asynchronous Storage: Uses
apply()rather thancommit()for non-blocking storage operations
7. Conclusion
The decompiled code analysis reveals a sophisticated malware implementation with advanced techniques for:
- Permission Acquisition: Social engineering via localized dialogs
- SMS Interception: Efficient broadcast receiver implementation
- Data Obfuscation: Multi-layer encoding with custom cipher
- Network Resilience: Online/offline operation with data caching
- Device Identification: Unique device fingerprinting for tracking
- Anti-Analysis: Heavy obfuscation of strings and control flow
These findings corroborate the assessment that this malware represents a significant threat, specifically targeting financial authentication via SMS interception and implementing robust mechanisms for data exfiltration.
- Title: Technical Analysis of Android Malware - Banking Trojan
- Author: Lee Wei Xuan
- Created at : 2025-05-11 21:19:53
- Updated at : 2025-05-25 14:06:08
- Link: https://weixuan0110.github.io/2025/05/11/Analysis-of-Malware-APK/
- License: This work is licensed under CC BY-NC-SA 4.0.